About Christina Lekati
Christina Lekati is a psychologist and a social engineer. She specializes in the mechanisms of behavior, motivation, decision making, manipulation and deceit. She is an expert in human dynamics and passionate about social engineering.
Christina has also a master’s degree in International Business. True to her passion, her thesis on social engineering strategies earned her a distinction during her graduation.
Contrary to typical career paths, her history and involvement in the security field started quite early in her life. Being raised by George Lekatis, a sought-after risk management and cyber security expert, she found herself magnetized by the security field at a very young age. Growing up, she was able to get involved in different projects that gave her an edge in her own knowledge and experience.
Christina has participated among other things in penetration tests, in trainings to companies and organizations, in vulnerability assessments, in profiling and analysis of the modus operandi, and in the process of identifying personality traits, behavioral tendencies, and demographic variables of offenders based on characteristics of illegal acts. She is working with Cyber Risk GmbH as a social engineering expert and trainer.
Christina is the main developer of the social engineering training programs provided by Cyber Risk GmbH. Those programs are intertwining the lessons learned from real life cases and previous experiences with the fields of cybersecurity, psychology, and counterintelligence. They often cover unique aspects while their main goal is to inspire delegates with a sense of responsibility and a better relationship with security.
Being committed to sharing knowledge and expertise, Christina is also a speaker. She participates in a variety of cyber security events, raising awareness and educating people on social engineering techniques and the psychological elements involved in human hacking.
She is also an active Advisory Board Member at the OSINT Curious project, contributing to the international scene of Open Source Intelligence (OSINT) with the latest news, updates and techniques on collection and analysis.
For updates, news, and insights, you can follow her on Twitter (@ChristinaLekati).
You may find some of Christina’s contributions to the international cybersecurity scene below:
1. Interview for the TAZ Newspaper (In German): Jeder hat eine Schwachstelle. Betrüger bauen Vertrauen auf, um an Daten oder Geld zu kommen. Welche Tricks sie dafür nutzen, erklärt Sicherheitstrainerin Christina Lekati.
https://taz.de/Sicherheitsexpertin-ueber-Social-Engineering/!5711020/
2. SANS Summit Talk for the Open Source Intelligence Summit (Washington DC): “Judging By The Cover - Profiling Through Social Media”. The talk demonstrates how attackers gather information on their targets through social media and utilize them to manipulate and victimize them – ultimately leading to a security breach. If you have a SANS account you may find the slides of the presentation by visiting:
https://www.sans.org/cyber-security-summit/archives
Alternatively, you may visit: (link where we have uploaded the slides)
3. Interview for Golem.de (In German): Social Engineering: Die unterschätzte Gefahr. Die größten Schwachstellen in technischen Systemen sind bis heute Menschen. Social Engineers machen sich ihre Sorglosigkeit zunutze - und finden auf sozialen Netzwerken alles, was sie für einen erfolgreichen Angriff brauchen.
https://www.golem.de/news/social-engineering-die-unterschaetzte-gefahr-1908-142812.html

4.Interview for the Dot Magazine: “Creating a “Human Firewall” for IT Security”. Psychologist and social engineer Christina Lekati from Cyber Risk GmbH explains the psychological basis of phishing and how to arm staff with effective defenses.
https://www.dotmagazine.online/issues/securing-the-future/human-firewall-for-it-security

5. Interview for the ECO Association- Europe’s Largest Internet Association (In German): Social Engineering: Mitarbeiter stärker für IT-Security sensibilisieren. Mitarbeiter müssen lernen, wie sie auf diese Anfragen in einer angemessenen Weise reagieren können. Dies geschieht durch intensive Schulung. Sie müssen verstehen, dass das Thema: Sicherheit geteilte Verantwortung bedeutet und, dass sie eben einen Teil dieser Verantwortung mittragen.
https://www.eco.de/news/social-engineering-unwissenheit-am-meisten-ausgenutzt/

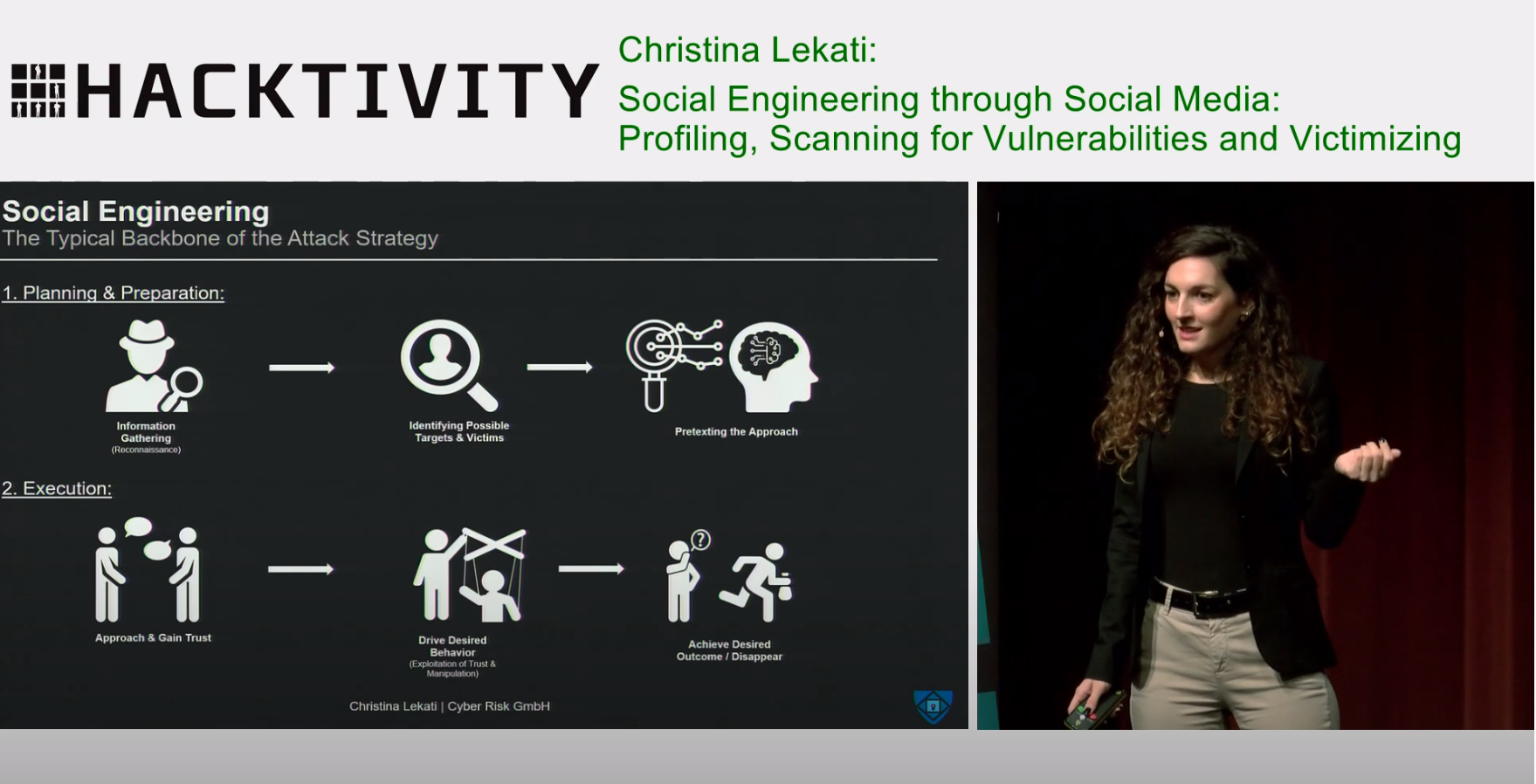
6. Conference Presentation at Hacktivity: "Social Engineering Through Social Media". The talk demonstrates how attackers gather information on their targets through social media and utilize them to manipulate and victimize them – ultimately leading to a security breach. https://www.youtube.com/watch?v=D8Z69AsSFn0&t=577s
7. Conference Presentation at ElBsides Hamburg: "When Your Biggest Threat is on Your Payroll – Drivers and Enablers of Insider Threat Activities". The talk discusses the organizational factors enabling insider threat operations and countermeasures against them, by combining the lessons learned on insider activity prevention from the fields of counterintelligence, psychology, and cyber-security.
https://www.youtube.com/watch?v=5ovY0YlLZNU&t=2208s

Our Services
Cyber security is ofter boring for employees. We can make it exciting.






